News Center
Global ransomware attacks are erupting. Learn about methods for preventing and handling ransomware.
Category: SUNNY News Publish Time:2017-05-14
Yesterday, a ransomware attack broke out in multiple countries worldwide, including the UK, Italy, and Russia. A large number of universities in China were also affected, with many students' and teachers' computer files being encrypted and requiring a ransom for recovery. According to an urgent announcement by 360 Security Guard, criminals used leaked NSA hacking tools to exploit Windows vulnerabilities, rapidly spreading ransomware such as ONION and WNCRY across campus networks. Computer users are advised to use the 360 "NSA Weapons Library Immunity Tool" for defense. Image: Ransomware infection phenomenon using NSA hacking tools. According to the 360 Security Center...
Yesterday, ransomware attacks broke out in multiple countries worldwide, including the UK, Italy, and Russia. A large number of universities in China were also affected, with many students' and teachers' computer files encrypted, requiring ransom payments for recovery. According to an urgent announcement from 360 Security Guard, criminals used leaked NSA hacking tools to exploit Windows vulnerabilities, rapidly spreading ransomware such as ONION and WNCRY across campus networks. Computer users are advised to use the 360 "NSA Weapons Library Immunity Tool" for defense.
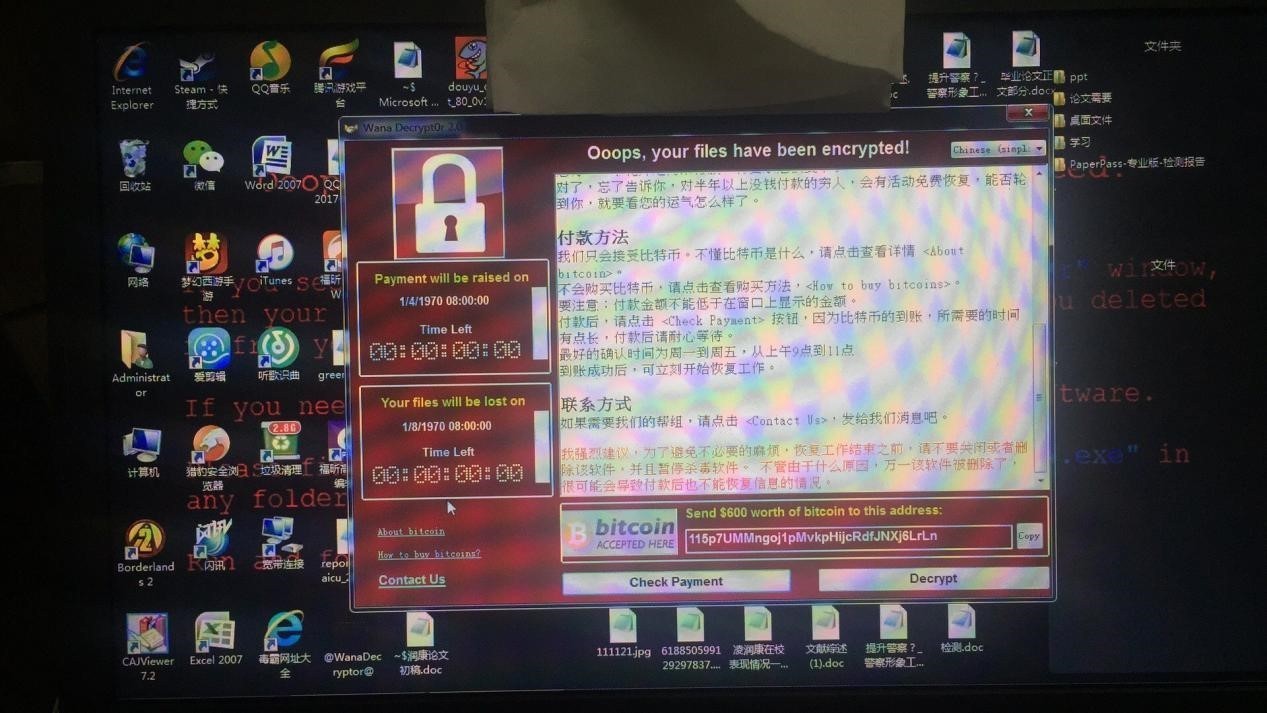
Image: Ransomware infection phenomenon caused by NSA hacking tools
According to 360 Security Center analysis, the ransomware attack on the education network was spread by the NSA-leaked "EternalBlue" hacking tool. "EternalBlue" can remotely attack Windows' 445 port (file sharing). If the system hasn't installed the March 2017 Microsoft patch, without any user interaction, simply by turning on and connecting to the internet, "EternalBlue" can execute arbitrary code on the computer, implanting ransomware and other malicious programs.
Due to previous instances of worm viruses using the 445 port in China, some carriers have blocked the 445 port for individual users. However, the education network has no such restrictions, with many machines exposing the 445 port, making it a prime target for criminals using NSA hacking tools. Coinciding with the university graduation season, the ransomware has encrypted and altered some graduating students' theses, directly affecting their graduation defenses.
Currently, the ransomware spread by "EternalBlue" mainly consists of the ONION and WNCRY families. The disk files of affected machines are modified with corresponding suffixes, making various files such as images, documents, videos, and compressed files inaccessible without paying a ransom to decrypt and restore them. The ransom amounts for these two types of ransomware are 5 Bitcoins and $300, equivalent to approximately more than 50,000 RMB and more than 2,000 RMB, respectively.
360's monitoring data on the education network ransomware incident shows that the ONION virus appeared first in China, with an average of approximately 200 attacks per hour, reaching over 1,000 attacks per hour during peak nighttime hours. The WNCRY ransomware was a new global attack that emerged on the afternoon of May 12th and quickly spread across campus networks in China, with approximately 4,000 attacks per hour during peak nighttime hours.
Security experts have found that the ONION ransomware also spreads with miners (computing virtual currency) and remote control Trojans, forming a "gift package" of malware combining mining, remote control, and ransomware. It specifically targets high-performance servers for mining profits, while encrypting files on ordinary computers to extort money, maximizing the economic exploitation of affected machines.
Microsoft released a patch in March 2017 to fix the Windows system vulnerabilities exploited by the NSA hacking tools. Previously, 360 Security Center also launched the "NSA Weapons Library Immunity Tool," which can detect and repair vulnerabilities exploited by NSA hacking tools. For systems such as XP and 2003 that have stopped receiving updates, the immunity tool can close the ports used by the vulnerabilities, preventing computers from being implanted with ransomware and other malicious programs by NSA hacking tools.
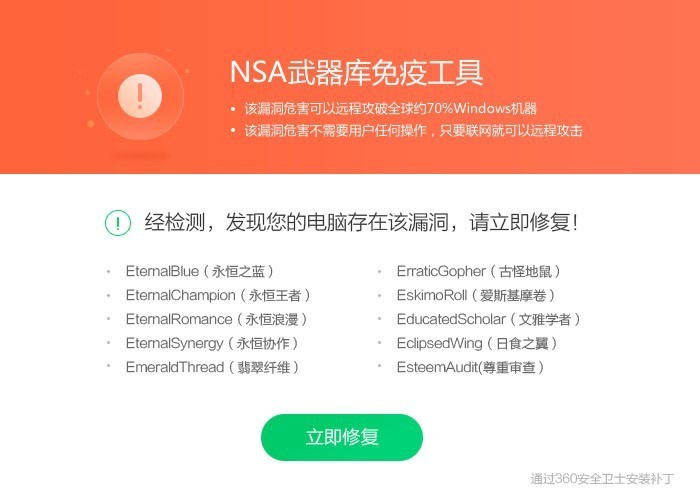
Image: NSA Weapons Library Immunity Tool
Confirmation method: Unplug the network cable, then turn on the computer. Confirm that 360 is running normally and Office is working correctly, then plug the network cable back in.
If not infected, immediately download the NSA Weapons Library Immunity Tool to patch and strengthen the system, and download Document Guard to back up documents.
Download NSA Weapons Library Immunity Tool:
Download Document Guard:
If infected, do not attempt to plug in a network cable or USB drive. Please follow the steps below:
1. Close computer TCP and UDP ports 135 and 445. Tutorial:
2. Install anti-ransomware protection tools and Document Guard, and attempt to recover encrypted files.
PS: Anti-ransomware protection tools are only effective before virus intrusion. Please back up important documents. Do not visit suspicious websites or open suspicious emails and files.
Keywords: Global ransomware attacks are erupting. Learn about methods for preventing and handling ransomware.
Related News
Shanli Technology's Bao Huang electroplating production line successfully put into operation
2023-04-23
Warm farewell to retiring employees
2019-12-03
Brave to "ping" Bo, "pong" moved my heart
2019-11-22
Professor Li Jiuling's Report on the Development of Zinc, Aluminum, and Magnesium Plated Sheets
2019-05-20
Shanli Co., Ltd. passed the new version of the quality management system certification audit
2017-07-24





 Wechat
Wechat