NEWS CENTER
The global outbreak of ransomware attacks, understand, prevent and deal with ransomware virus methods
- Time of issue:2017-05-14 01:52
(Summary description)Yesterday, ransomware attacks broke out in many countries around the world such as the United Kingdom, Italy, Russia, and a large number of universities in China were also infected. The computer files of many teachers and students were encrypted by viruses and can only be recovered by paying a ransom.
The global outbreak of ransomware attacks, understand, prevent and deal with ransomware virus methods
(Summary description)Yesterday, ransomware attacks broke out in many countries around the world such as the United Kingdom, Italy, Russia, and a large number of universities in China were also infected. The computer files of many teachers and students were encrypted by viruses and can only be recovered by paying a ransom.
- Categories:SUNNY News
- Author:
- Origin:
- Time of issue:2017-05-14 01:52
- Views:
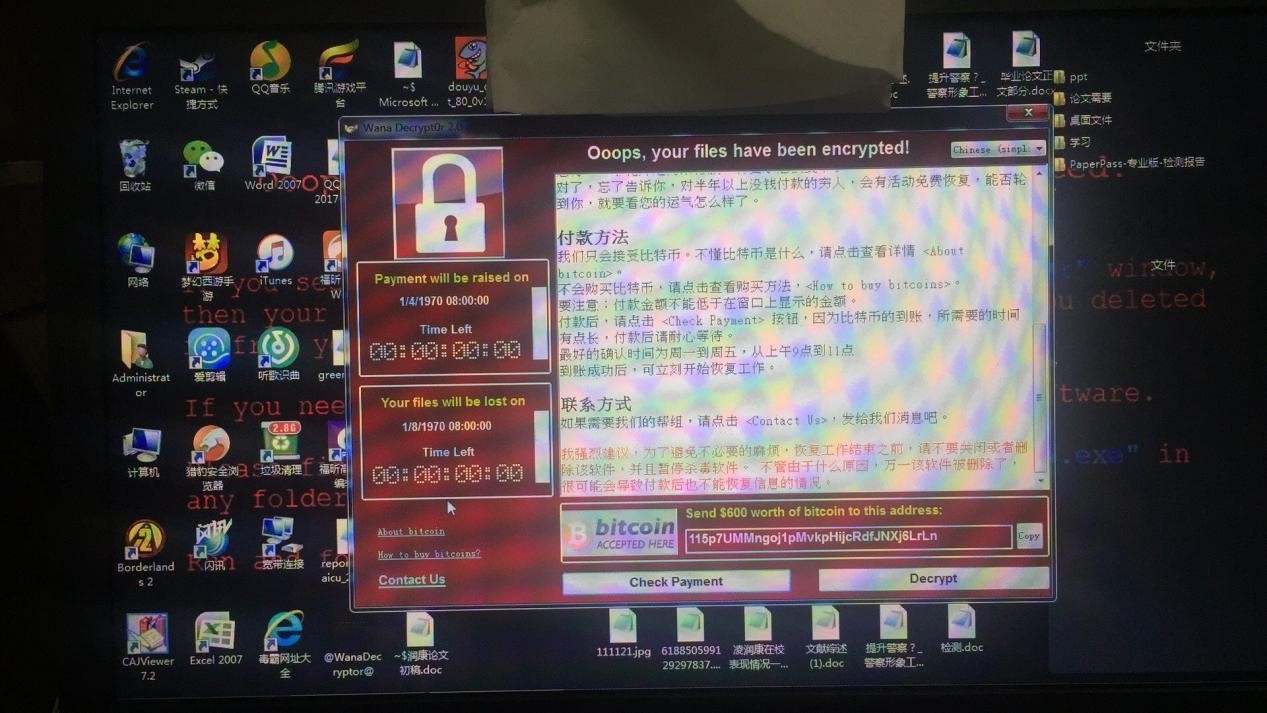
According to the analysis of 360 Security Center, the education network ransomware was spread by the "Eternal Blue" hacker weapon leaked by the NSA. "Eternal Blue" can remotely attack Windows port 445 (file sharing). If the system does not install the Microsoft patch of this year, no user operation is required. As long as the system is turned on and connected to the Internet, "Eternal Blue" can execute any code on the computer. , Implanting malicious programs such as ransomware.
Because there have been many worms spreading through port 445 in China, some operators have blocked port 445 for individual users. However, Education Network does not have this restriction. There are a large number of machines with port 445 exposed, so it has become the hardest hit area for criminals using NSA hacker weapons. It is the graduation season of colleges and universities, and the ransomware has caused some recent graduates' thesis to be encrypted and tampered with, which directly affects the graduation defense.
At present, the ransomware spread by "Eternal Blue" is mainly based on the ONION and WNCRY families. The disk files of the victim machine will be tampered with the corresponding suffixes, and various materials such as pictures, documents, videos, and compressed packages cannot be opened normally. , Only the ransom can be decrypted and restored. For these two types of ransomware, the amount of ransomware is 5 bitcoins and 300 US dollars, which is equivalent to RMB 50,000 and 2,000 yuan respectively.
360 monitoring data for the education network ransomware incident showed that the ONION virus appeared first in the country, with an average of about 200 attacks per hour, and the peak at night reached more than 1,000 per hour; WNCRY ransomware was a new appearance in the afternoon of May 12 The global attacks have spread rapidly across China’s campus networks, with about 4,000 attacks per hour during peak hours at night.
Security experts have discovered that ONION ransomware will also spread with mining machines (computing to generate virtual currency) and remote control Trojan horses, forming a Trojan horse virus "big gift package" that integrates mining, remote control, and ransomware. It is specially selected. High-performance servers are mining for profit, and ordinary computers will encrypt files to blackmail money, maximizing the economic value of the victim machine.
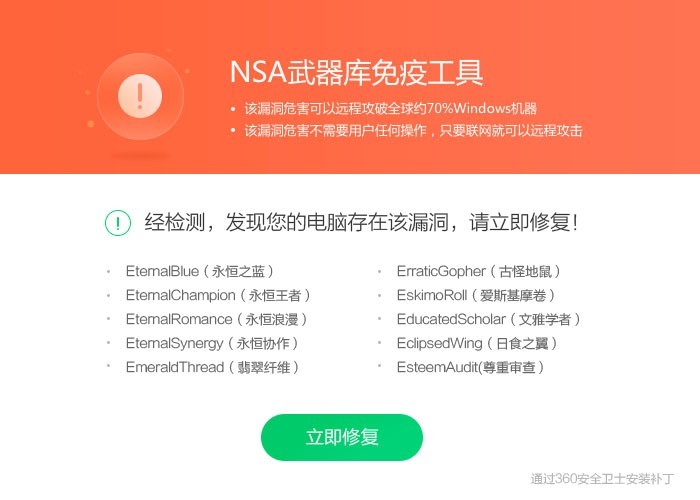
For the Windows system vulnerabilities used by NSA hacker weapons, Microsoft released a patch in March this year. Previously, the 360 Security Center has also launched the "NSA Weapon Library Immunization Tool", which can detect and repair vulnerabilities in NSA hacker weapon attacks with one click; for systems that have stopped updating XP, 2003, etc., the immunization tool can close the exploited ports to prevent computers from being compromised. NSA hacker weapons implant malicious programs such as ransomware.
Confirmation method: first unplug the network cable and then turn it on, confirm that the 360 is operating normally and the office is normal, and then plug in the network cable.
If there is no poisoning, immediately download the NSA weapon library immunization tool to patch and strengthen the system, and download the backup file of the document guard
PS: Anti-ransomware protection tools only work before the virus invades. Please do a good job of backing up important documents. Do not visit suspicious websites, do not open suspicious emails and files
Hot News

黄石山力科技股份有限公司
Sunny Technologies Incorporation Limted

Contact us
Add:No. 2, Guangzhou road, tuanshancheng Development Zone, Huangshi City, No. 101, Gaoxin 6th Road, Donghu New Technology Development Zone, Wuhan
Mail:spt@sunnychina.com.cn
Tel:156 7177 7755 / 027-59715061
Fax:027-59715060






